ALBAWABA – Big tech companies Google, Amazon and Cloudflare said the biggest-ever DoS attack has been ongoing since August and could disrupt the interest, Reuters reported Wednesday.
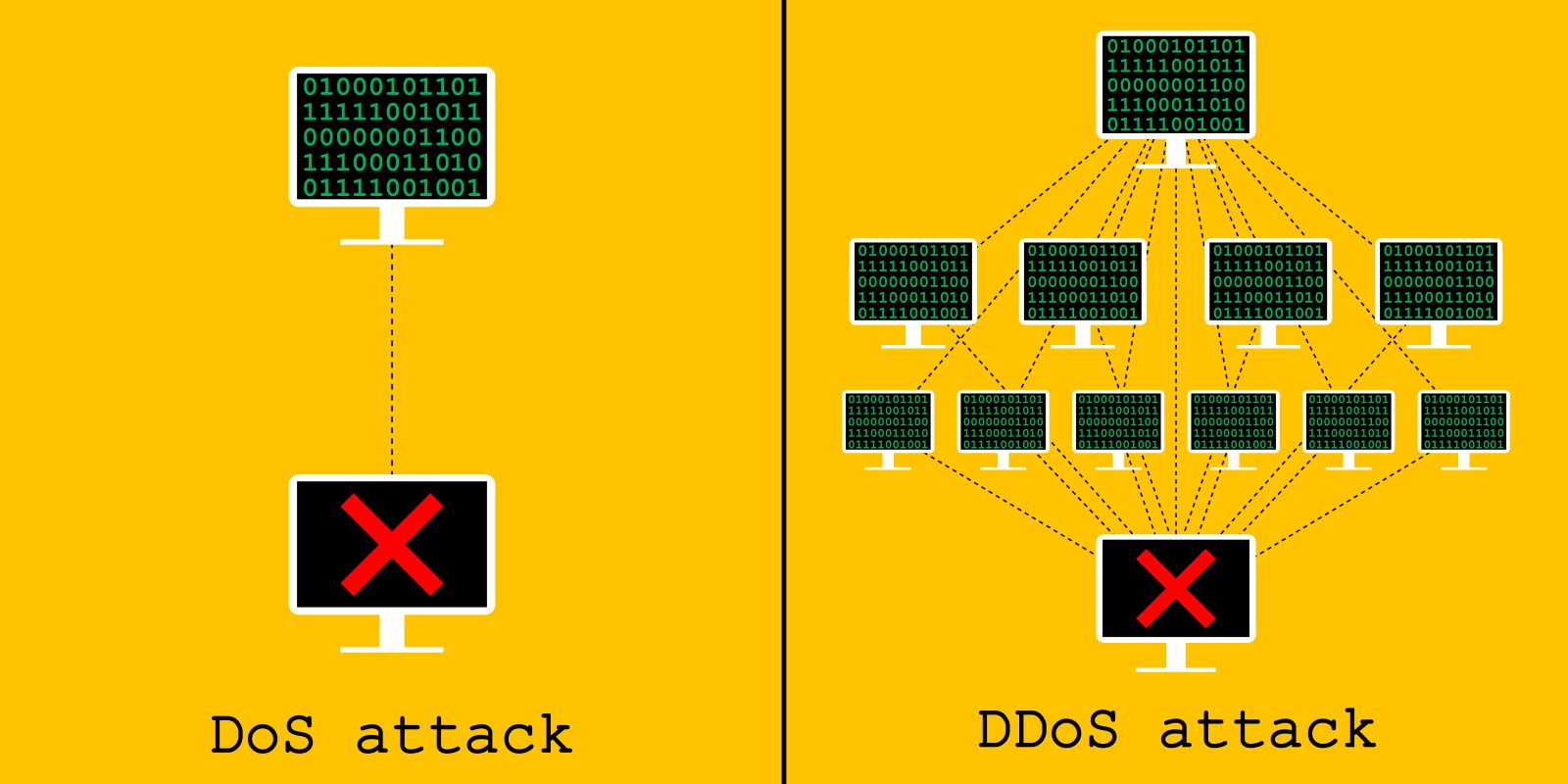
Denial of service (DoS) attacks are done by flooding servers and overwhelming them with requests so much that actual users can no longer access the websites hosted on these servers.
However, a new technique has been used to recycle one of the oldest, most basic forms of cyberattacks.
This biggest-ever DoS attack was enabled by new weaknesses in the face of new technologies and techniques - Shutterstock
As the online world developed, so too did the power of denial-of-service attacks. Millions of bogus requests per second can be generated to deny other users access to the online service, which resulted in the biggest-ever DoS attack.
This is the biggest-ever DoS attack
The recent attacks measured by Google, Cloudflare and Amazon show that the perpetrators were capable of generating hundreds of millions of request per second.
In a blog post on Tuesday, Google said that its cloud services were able to fend off an avalanche of rogue traffic more than seven times the size of the previous record-breaking attack thwarted last year.

The people behind the biggest-ever DoS attack are still unknown - Shutterstock
Likewise, internet protection company Cloudflare Inc. said the attack was "three times larger than any previous attack we've observed". And Amazon.com Inc.'s web services division also confirmed being hit by "a new type of distributed denial of service (DDoS) event."
All three said the attack began in late August; and Google confirmed it was ongoing, according to Reuters.
The biggest-ever DoS attack was enabled by HTTP/2
All three companies said the supersized attacks were enabled by a weakness in HTTP/2 – a newer version of the HTTP network protocol that underpins the World Wide Web, Reuters reported. The new network protocol reportedly makes servers particularly vulnerable to rogue requests.

This biggest-ever DoS attack is not fundamentally different from the customary DoS attacks as the function is the same - Shutterstock
The firms urged companies to update their web servers to ensure that they do not remain vulnerable.
None of the three companies said who was responsible for the attacks, which have historically been difficult to pin down. But Google’s blog post said that in only two minutes, the attackers "generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023". Cloudflare said the attack was of a magnitude that "has never been seen before."
If cleverly aimed and not successfully countered, such attacks can lead to widespread internet disruption, Reuters warned. In 2016, an attack attributed to the "Mirai" network of hijacked devices hit domain name service Dyn, disrupting a swathe of high-profile websites.








